AccessPatrol - Data Loss Prevention Overview
With the rise of portable storage devices and removable media, data theft is becoming an increasing threat to organizations. Devices such as USB keys, Wi-Fi connections, FireWire ports, Bluetooth devices, iPod, mobile phones and MP3 players are connecting seamlessly to the company networks.
Most IT administrators have no control over the connection of these portable storage devices, leaving company confidential information exposed. Access Patrol provides a comprehensive solution for securing company computers to restrict unauthorized access from personal external storage media to steal your company's proprietary information.
AccessPatrol provides an effective method for power management. With a simple click of the mouse, computers can be remotely shutdown or booted. This function can also be scheduled to force a shutdown of the computers at a specific time or schedule a boot of the computers at the beginning of a work day.
Features

Control Access of External Devices
AccessPatrol will allow the administrator to control the access security of the following devices:
- USB (Removable disk, iPod),
- CD/DVD,
- Floppy, Tape,
- External Hard Drives,
- Firewire,
- Memory cards and more.

Centralized Security Console
With a few simple clicks, endpoint security can be readily implemented through the centralized console. The web based console, provides the additional benefit of being able to access the console from any location.

Device Allowed List
Devices that are added to the Allowed List can allow users access to only company authorized devices. Users would have read/write privileges to those devices listed under the Allowed List.

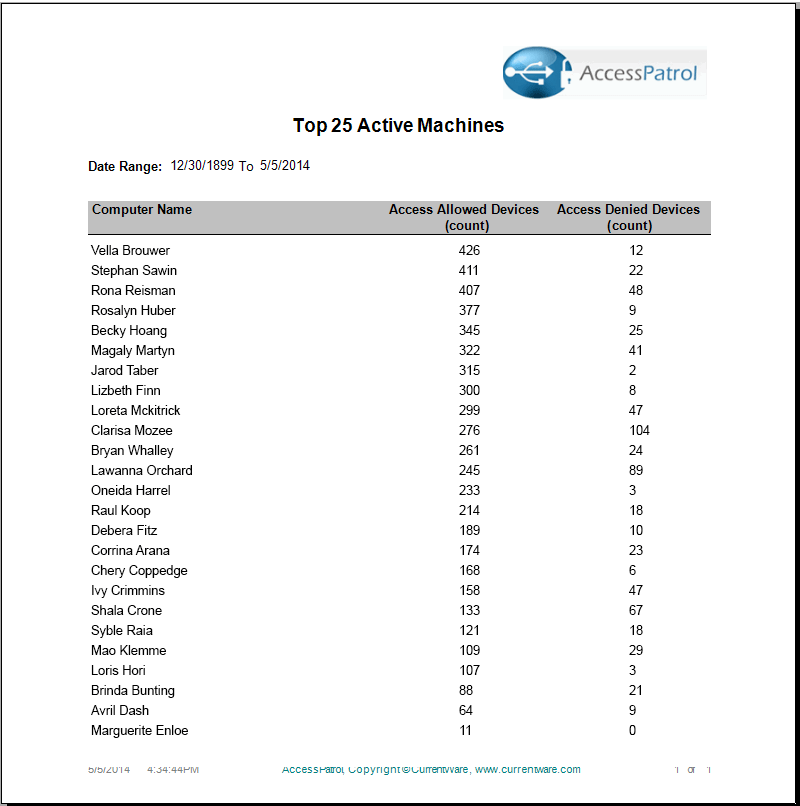
Device Reports
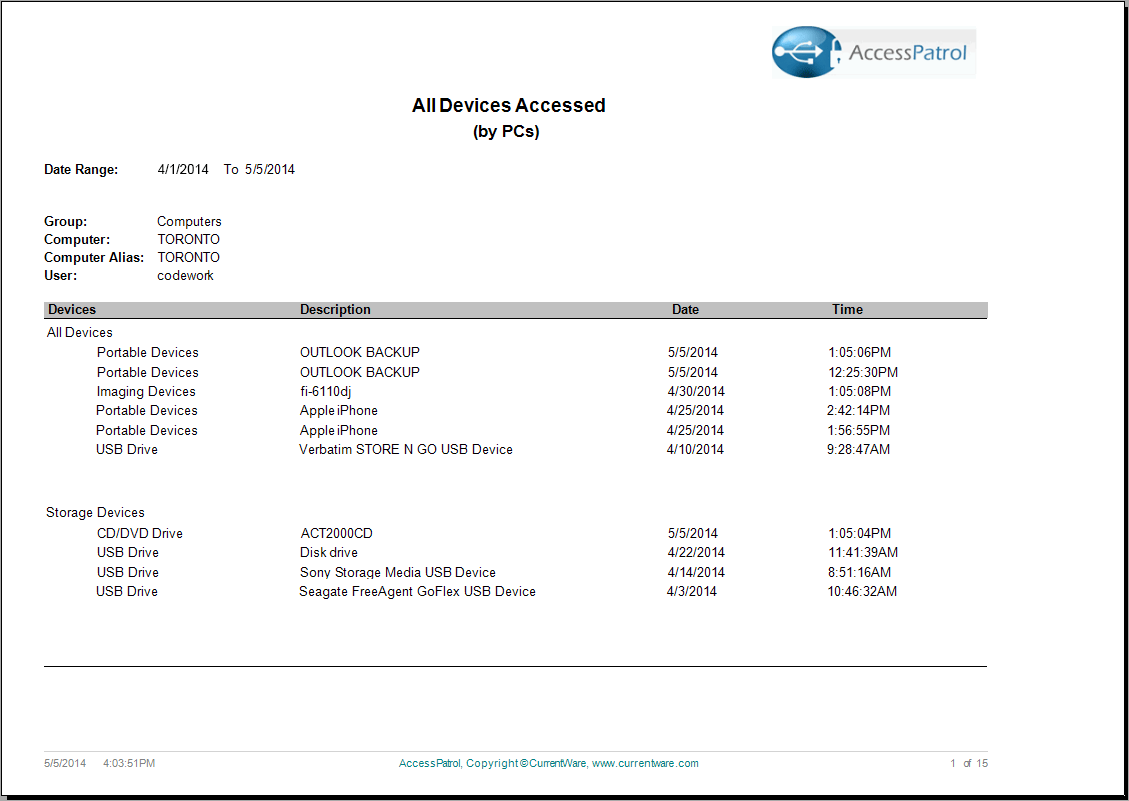
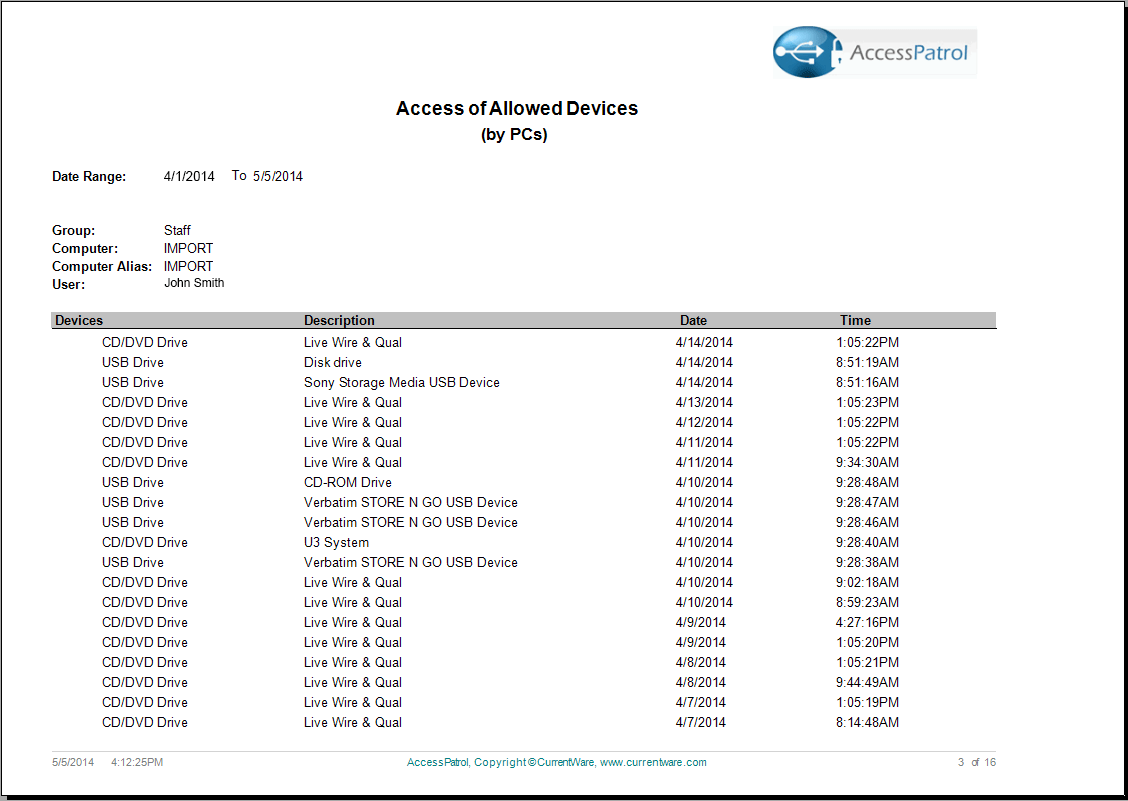
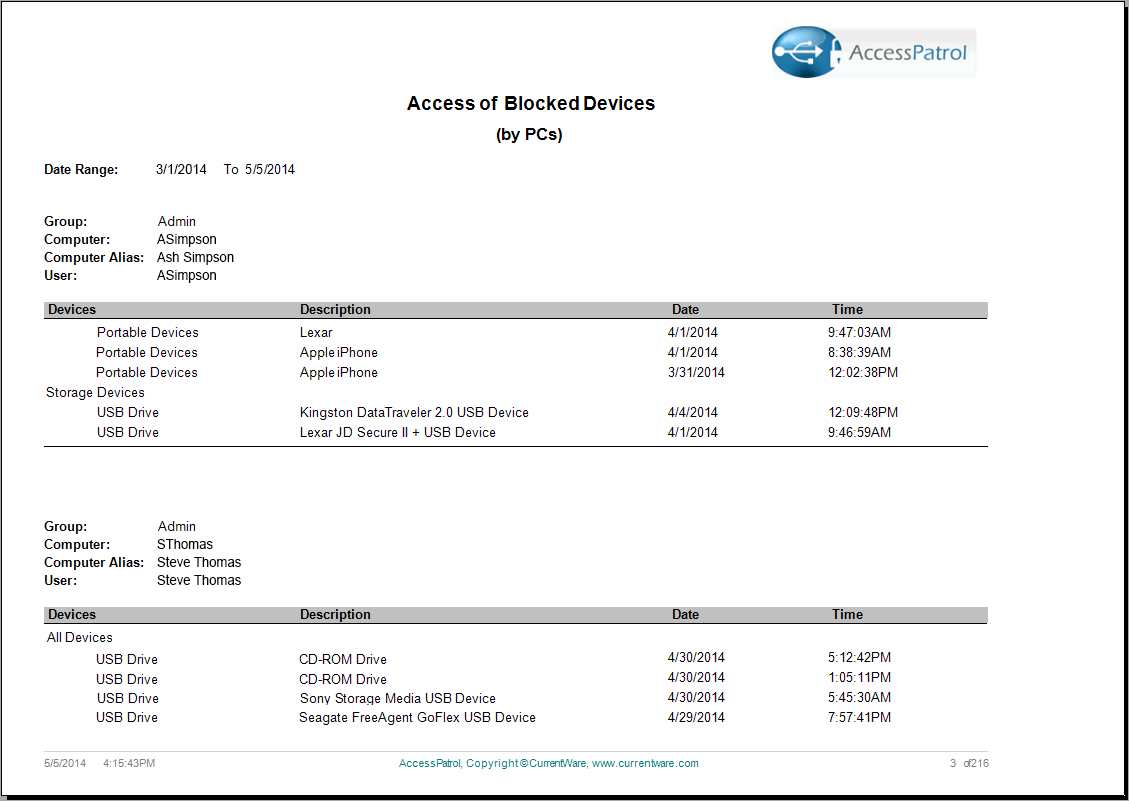
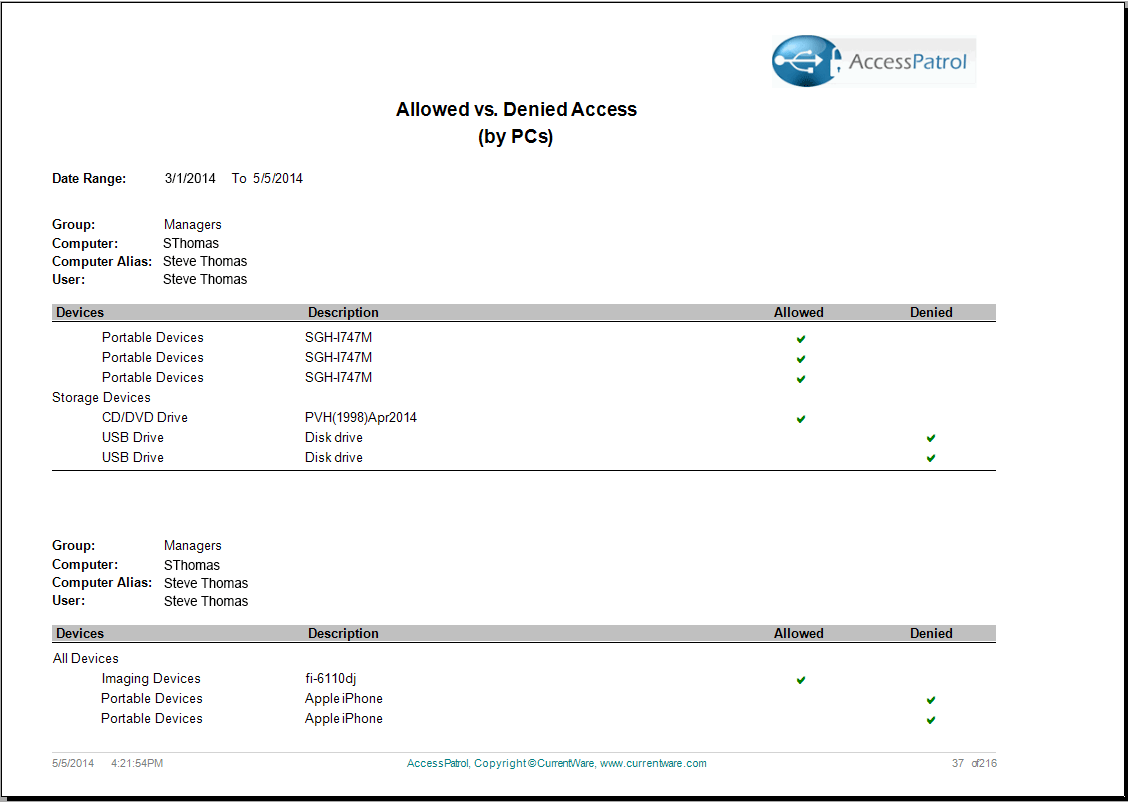
Choose from our various reports to analyze removable device usage and identify employees that frequently abuse the endpoint device policies. Using the intuitive reporting tool, generate comprehensive reports that highlight device usage by computer or user. The AccessPatrol reports are clear and easy to understand, ranging from executive level summaries to drill down detailed reports for administrators. The reports include:

Email Reports
For additional analysis of removable device access, make use of the handy email reports function. Schedule a time and date for a report to be sent directly to your inbox.
Additional Features
- Allowed List: a white list that defines a number of devices that are allowed to be accessed by the users, while blocking all other USB and external devices.
- Device Permissions Scheduler: Users can be assigned access to devices at specific times. Through the Scheduler feature, access privileges can be allocated for all or specific devices.
System Requirements
Here's the link to the system requirements for AccessPatrol